Data Leaks Escalate
As Data Leaks continue to mount online this year, dealing massive impacts to the companies and governments they are stolen from, hackers have become increasingly public about their activities and continue to act with impunity in the cybercrime underworld. After being down for a brief period after the arrest of its administrator, Breach Forums has returned with a vengeance, boasting large leaks for free and for sale on a daily basis. An infamous hacktivist group known as ‘SiegedSec’ just wrapped up an aggressive offensive campaign called #OpColombia against the Colombian government and has now set its sights on the U.S. in a new campaign, yet to be named by the group. Users continue to post SiegedSecs data for free to Breached as a means of mass-distribution.
Most Recent Leak of U.S. Government Data
‘SiegedSec’ itself announced yesterday a slew of new successful compromises and defacements in its campaign targeting U.S. States. A screenshot of their announcement is included below:
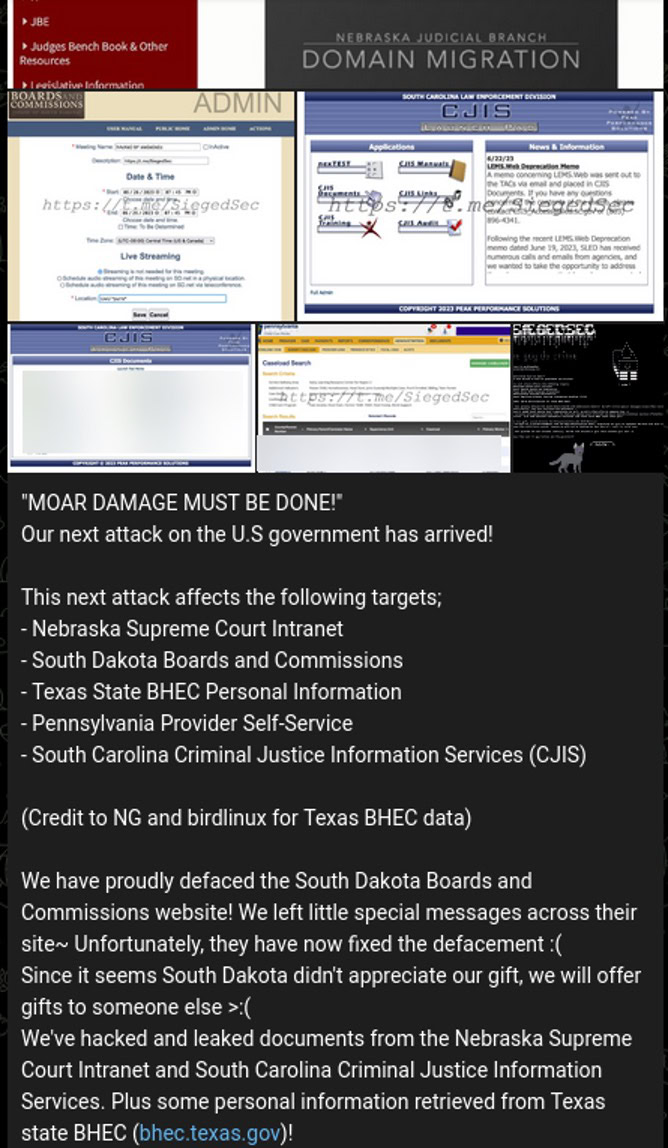
Fig. 1: Post by SiegedSec regarding their latest leaks on Telegram.

Fig. 2: Content being reposted by BreachedForums user Tanaka.
The leak published yesterday contains a compilation of data from the following targets:
- The Nebraska Supreme Court Intranet
- The South Dakota Boards and Commissions data
- Texas State Behavioral Health Executive Council (BHEC) data
- Pennsylvania Providers Self-Service portal data
- South Carolina Criminal Justice Information Services (CJIS) Data.

Fig. 4: Raw data from the leaks
Samples shown by Tanaka in the listing for the data leak contain full names, addresses, social security numbers, dates of birth, among a wide variety of data types and categories spread through the various leaks.
SiegedSec U.S. Campaign Origins
This campaign started last week, when Sieged posted an announcement that it would be targeting U.S. States. Its first victim was the Fort Worth local government. They publicly leaked what they claim to be all data hosted on Fort Worths government website resources. This included:
- employee lists
- work orders
- invoices
- police reports
- internal emails
- internal files
- CCTV camera footage
- ‘lots, lots, lots more’

Fig. 5: Original post by SiegedSec to Telegram announcing their new campaign

Fig. 5: Breached Forums user Tanaka posting the forth worth leak
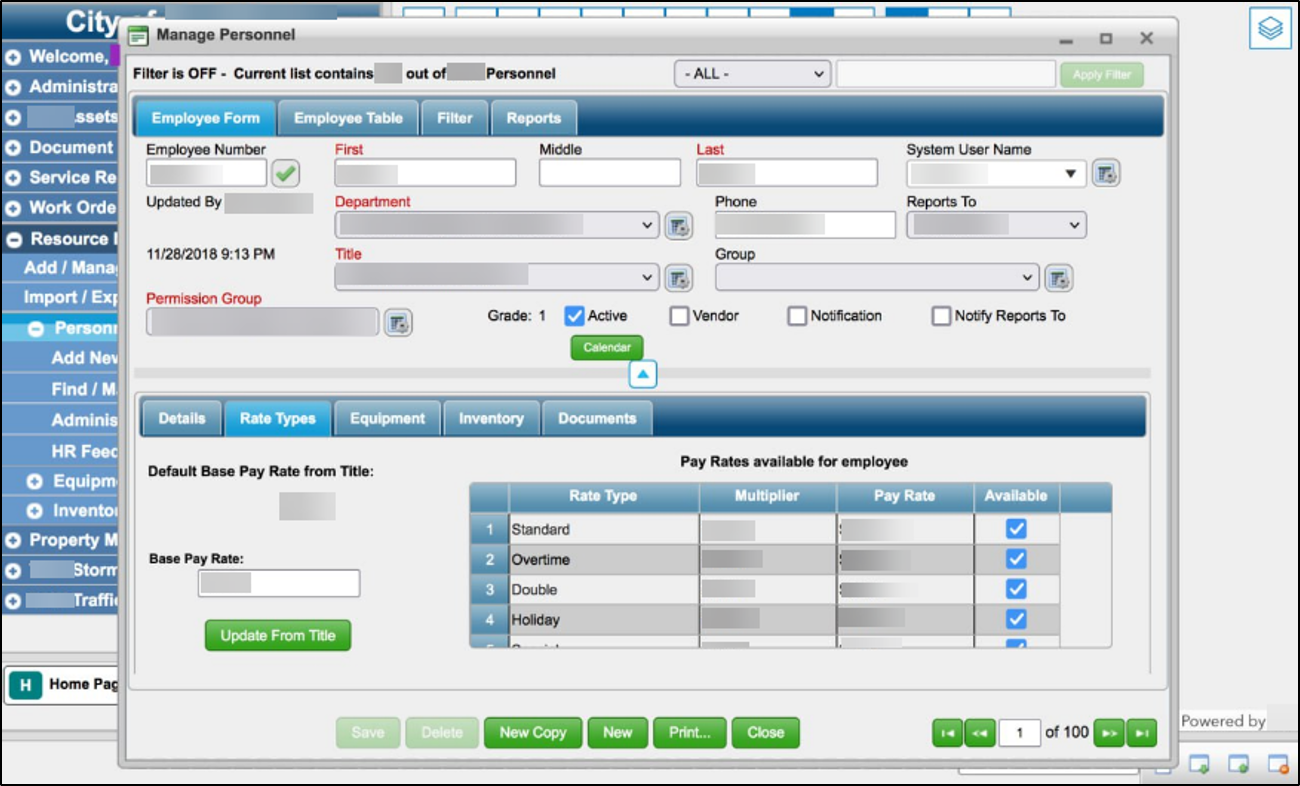
Fig. 5: Screenshot from the Forth Worth leak, showing an employee management admin panel.
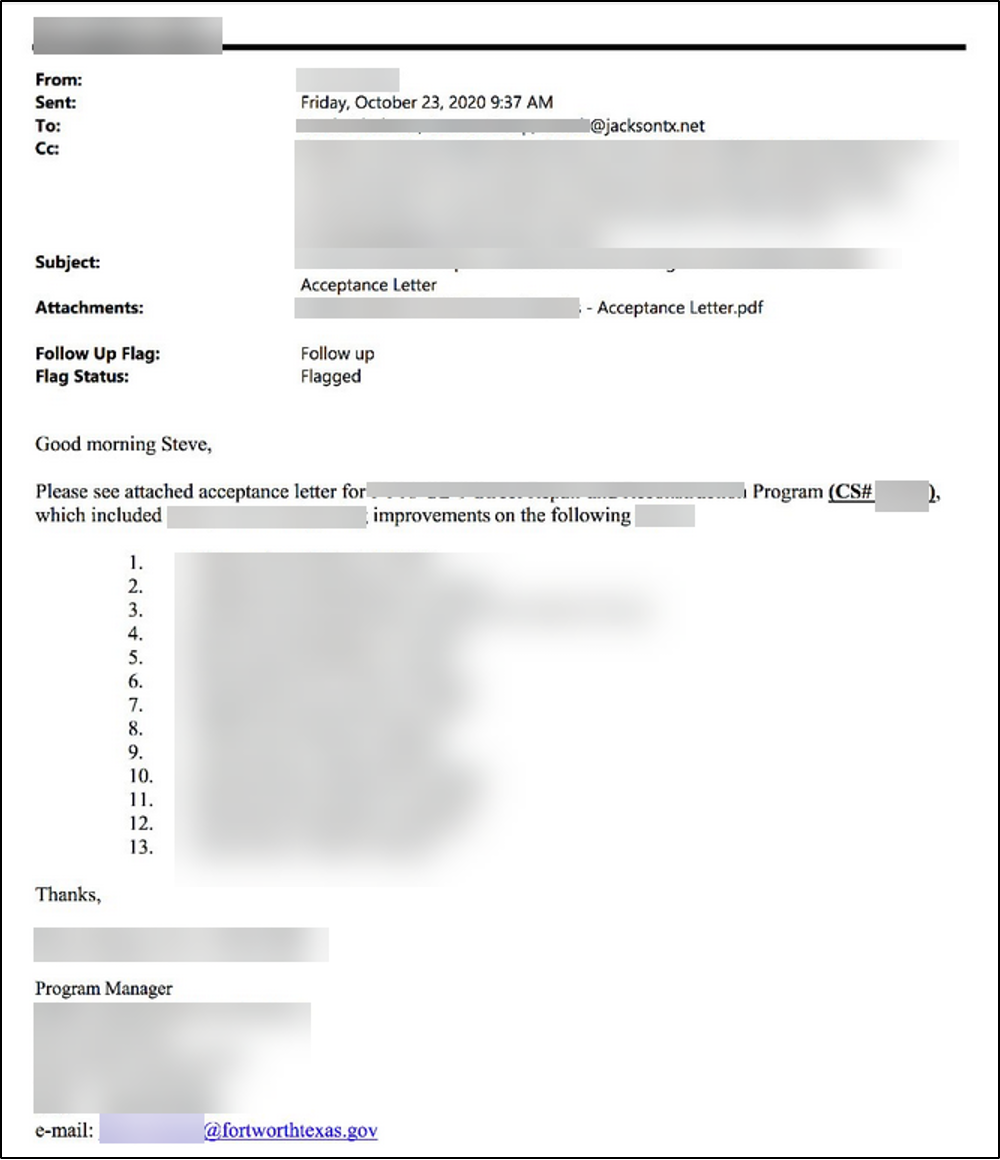
Fig. 6: Screenshot taken from the Forth Worth leak, showing an internal email between Forth Worth government and contractors.
This campaign continues to leak more data on a near daily basis and is an actively developing situation. Foretrace continues to monitor the extent and frequency of the leaks to determine the scale of impact and notify its customers should they be impacted.
Who is SiegedSec?
SiegedSec is an offensive hacktivist cell. SiegedSecs missions thus far have involved leaking stolen data and defacing the resources of its targets. Its most notable targets before this campaign have been a variety of commercial and government organizations in Russia, which Sieged claims to have knocked offline, along with a variety of smaller campaigns targeting South American governments, software companies, and healthcare providers.
Due to the hacktivist nature of SiegedSec’s operations, they do not have a financial motive behind these attacks and are not asking for money from their victims. When communicating with victims, the leader of SiegedSec, YourAnonWolf, cites ‘fun’ or ‘lulz’ as a primary motivator.
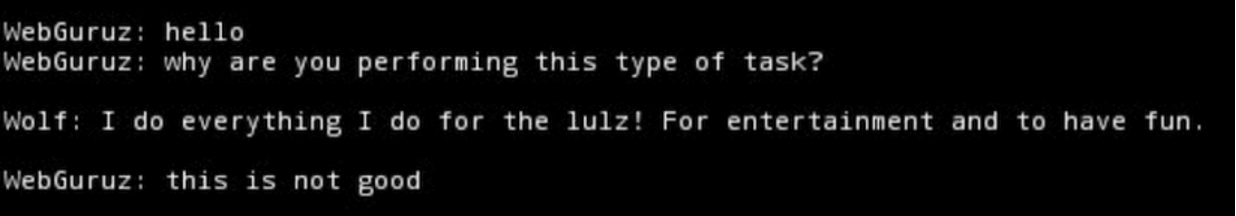
Fig. 3: Leaked screenshot of chat logs between an old victim of Sieged, WebGuruz, and the leader of SiegedSec, shown here as Wolf.
Impact and Trends
Victims
This is just the beginning of SiegedSec’s campaign against U.S. states, and the full extent of its impact is still not fully understood, as the leaks present a tremendous amount of data to be analyzed. This campaign is only two weeks old, and these operations can last for months or years. The obvious impacts are the citizens of these states who have had their personal information, in some cases down to detailed medical records and law enforcement communications, leaked. These leaks do not sit behind a paywall and are free to access and download. The impacts of that data being public will be felt by the victims likely for many years, as they have become easy targets for identity theft which is experiencing a resurgence due to increasing data leaks.
These leaks also contain information about public infrastructure, development projects, government priorities, etc. While they aren’t exactly nuclear codes, this private data is now freely and openly accessible to nation state adversaries who can use it to build informed understandings of U.S. infrastructure and operations.
Institutional Trust
Trust in governments and commercial entities to protect the data they are entrusted with by their users or citizens continues to wane. Public incidents like this, which appear to be executed with speed and ease by hacktivist groups, send a strong message to citizens and users that in many cases, even basic controls or detection strategies have not been put in place to prevent the exposure of their data.
Ease of Access
SiegedSec appears to be ripping through the U.S. States’ digital infrastructure with ease. In a matter of weeks, accessing hundreds of thousands of internal files and communications, administrative panels for a variety of services, and large collections of PII. The speed with which they operate illustrates the severe lack of data leak detection and prevention strategies implemented in the increasingly public digital footprints of the targeted states. This trend is also observed in the private sector as massive data leaks continue to mount month to month.
Recommendations:
Data Leak Detection
In an overwhelming majority of data leaks from this year, the data being sold or posted was discovered by cyber criminals or researchers in the public, often by finding exposed storage buckets that have been misconfigured to be publicly accessible. Using these adversarial enumeration techniques against your own organization and its infrastructure is key to detecting such leaks within your own environment before they become a breach or public incident.
Tailored Red Team Engagements
Another tried and true method for understanding how an adversary can move about your environment or public resources is engaging firms for red team and/or penetration testing exercises. Engagements in the coming months and quarters should emphasize the attacks adversaries have been leveraging in the wild to compromise data, with a focus on exposed data and cloud hosted infrastructure and storage.
Foretrace provides data exposure detection capabilities to help our customers detect data leaks and exposures before they become costly data breaches. Follow Falre on Twitter and Linkedin to stay updated on our data leak research.



